Apr 25, 2023
Discovering the Secrets of the Dark Web Market

To access the dark web, there are two methods that can be combined for added security: using Tor over VPN. This involves connecting to a VPN first before accessing the Tor network. It is important to note that free versions of these services may result in slow connection speeds, limited data usage, and potential security vulnerabilities.
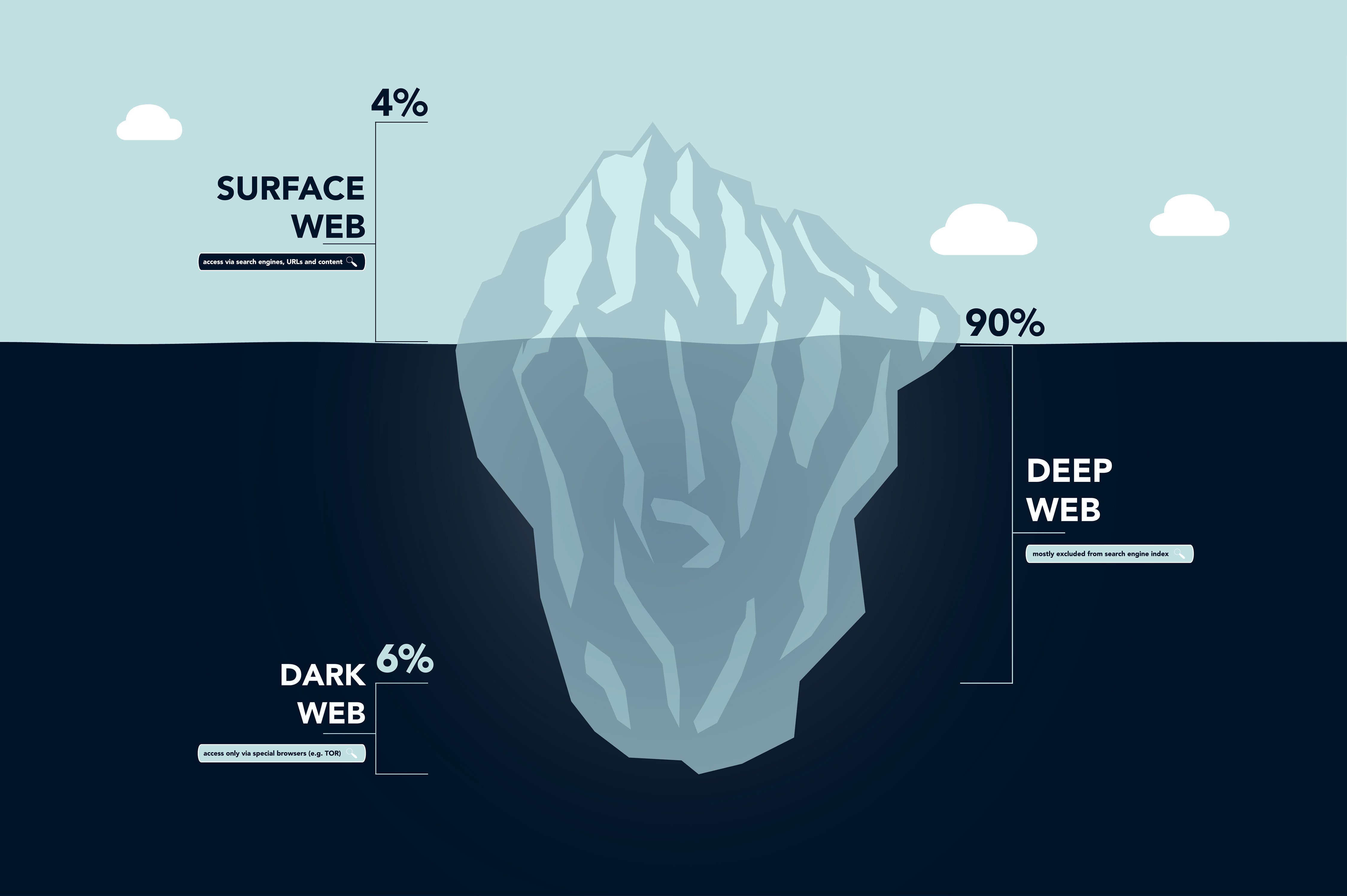
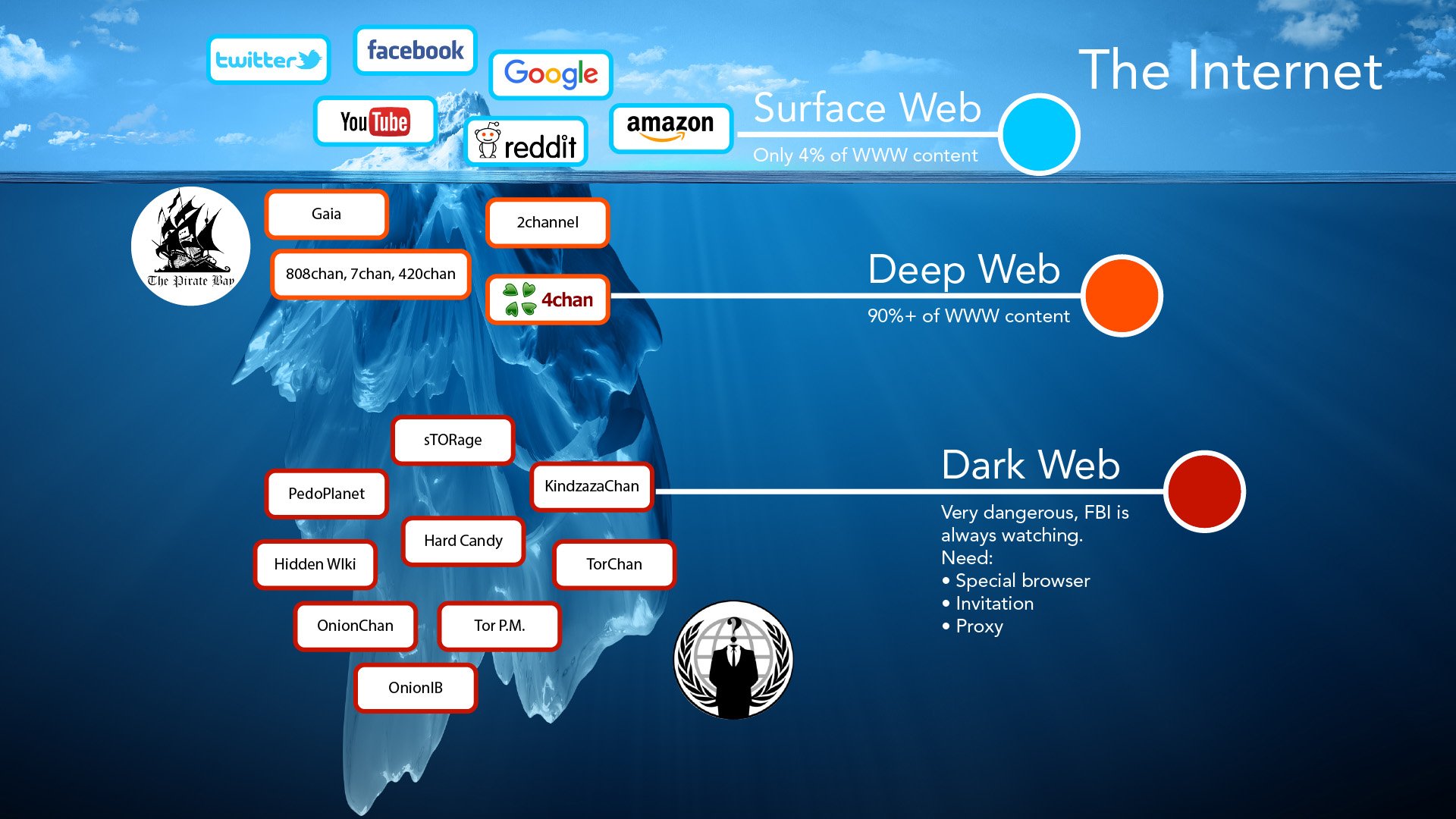
Googles latest official update also included information about the number of pages in their database. The deep web, which is often referred to as the invisible or hidden web, constitutes the majority of the web. Another area of the web is the dark web.
Accessing the dark web can be a risky endeavor, but for those who have a specific purpose in mind, it can be a valuable resource. However, it is important to approach the dark web with caution and take steps to protect your identity and data. One should only access the dark web if they have a clear intention and are willing to take the necessary precautions to ensure their safety. Remember to always be mindful of your purpose and stay vigilant when navigating the dark web.
Accessing the dark web can be a risky venture, as the information found there can be used against you. The data gathered from various sources, including your own device, can eventually lead to your complete exposure, and even the police showing up at your doorstep. To minimize the risks, it's recommended to turn off your location on your device before accessing the dark web. Think of the deep web as the vast, unexplored depths of the ocean, with both hidden treasures and potential dangers lurking beneath the surface.
Accessing the dark web requires a certain level of expertise, which includes knowledge of private and encrypted email services, instructions for installing an anonymous operating system, and advanced tips for maintaining privacy. It is important to have a clear understanding of the information you are seeking and your reason for accessing the encrypted web. To ensure maximum protection, it is recommended to use a VPN in addition to the Tor network's existing security measures.
According to Wired author Andy Greenberg, the deep web comprises about 90% of the internet, whereas the dark web only accounts for approximately 1%. This section of the web is specifically created to ensure the privacy and anonymity of both users and website owners.
Securely Navigating the Shadowy Depths of the Dark Web with Dark Web Monitor
Editors' Recommendations: To access the dark web, simply boot your computer from the Tails USB stick. It is recommended to use a VPN over Tor, which should be opened before connecting to a VPN.
Ensure that you have closed all apps that could potentially monitor your activities when attempting to access the dark web.
Although accessing the dark web can be challenging, there are resources available to help you navigate it. Manual configuration of I2P can be a daunting task, often requiring adjustments to your router console and browser proxy settings. Fortunately, the I2P website provides configuration packages for a variety of device platforms. To access the dark web safely, it is important to exercise caution and avoid clicking on unfamiliar links. This step-by-step guide can help you determine if your security has been compromised and navigate the hidden depths of the internet.
Dark web accessing can be a daunting task for many, but with the help of Deep web, a web browser based on Firefox that is freely available for use, it can be done relatively safely. Additionally, there are various tools at your disposal which can be used to monitor the dark web and scan for any personally identifiable information that may have been compromised, or even to respond to any potential attacks.
The aim of Google is to reduce the duration of user's search for specific queries. It's crucial to ensure that the Tor file you download is from their official website. Always acquire the newest version and keep it updated.
Securely access the dark web, disconnect from TOR and Tails once you have obtained what you require, and then log out.
Navigating the Depths of the Dark Web: A Guide to Accessing and Monitoring
Accessing the dark web can be a daunting task, but it is not impossible. However, the process of installing the necessary tools can be quite challenging. You will need a router that is compatible with the Tor network, which can be a bit tricky to find. Once you have the right router, you will need to configure your browser for privacy and security. This can be done by accessing the settings and selecting the appropriate options. With the right tools and a bit of patience, you can access the dark web and explore its contents.
If you have already enabled the safety settings on Tor, accessing the dark web won't require you to disable any scripts as they are already turned off.
When it comes to accessing the dark web, DuckDuckGo is a great option as it doesn't monitor your activity and provides links to websites on its results page. If you want to visit Onion/wiki/Main_Page, which only works on dark web browsers, DuckDuckGo can help you get there. Additionally, ransomware packages are often distributed through the dark web by affiliates.
Discovering the dark web can be a daunting task, but accessing it safely is crucial. Here are some valuable tips to help you navigate the dark web with caution:
1. Use a VPN: A Virtual Private Network (VPN) can provide you with an added layer of security by masking your IP address.
2. Use Tor Browser: The Tor Browser is the most popular browser used for accessing the dark web. It encrypts your traffic and helps you remain anonymous.
3. Disable JavaScript: Disabling JavaScript can help prevent malicious code from running on your device.
4. Use encrypted email: Encrypted email services like ProtonMail can help keep your communications secure.
5. Use a secure password: Use a strong and unique password for your dark web accounts to prevent unauthorized access.
6. Avoid illegal activities: The dark web is known for illegal activities, so it is best to avoid them altogether.
7. Use common sense: Be cautious of suspicious links and offers that seem too good to be true.
8. Keep your device updated: Keep your device updated with the latest security patches to prevent vulnerabilities.
9. Use a separate device: Consider using a separate device solely for accessing the dark web to prevent any potential security breaches on your main device.
According to Tiquet, the dark web has played a crucial role in the rise of Bitcoin, and vice versa. Bitcoin, although widely recognized as the top cryptocurrency, is not without its vulnerabilities. Dark web access has enabled the proliferation of Bitcoin, but users should exercise caution when engaging with this underground network.
Safely Navigating the Shadows: Accessing and Monitoring the Dark Web
If you're interested in accessing the dark web, there are a few commonly asked questions that you may have. Here are some answers to help you navigate this mysterious corner of the internet. To begin, it's important to note that accessing the dark web comes with risks and potential consequences. However, if you're willing to take that risk, there are steps you can take. First, you'll need to open the Tor browser. It's worth noting that the terms "dark web," "deep web," and "dark net" are often used interchangeably, but they do have distinct differences. Despite this, they share some common ground.
Hit the Enter key and you'll be able to access DuckDuckGo's no-tracking search service for the dark web through the Tor browser. This is a valuable tool for gathering information about the dark web. Visit org/ for more details.
Verify if the current value displays a decrease and the status reads as modified. It is possible to purchase login credentials, including usernames and passwords. The service provides two options: darknet and opennet modes.
Accessing the dark web can lead you to various whistleblower sites, including a version of Wikileaks specifically designed for the dark web. However, it's important to note that the dark web is also where most botnet hackers choose to sell the data they've mined or even offer access to an dark web accessing entire botnet.
Explore further
Distributed by Iceball, LLC.