May 03, 2023
Discover the Mysterious World of I2P Darknet and Explore the Heineken Express Market
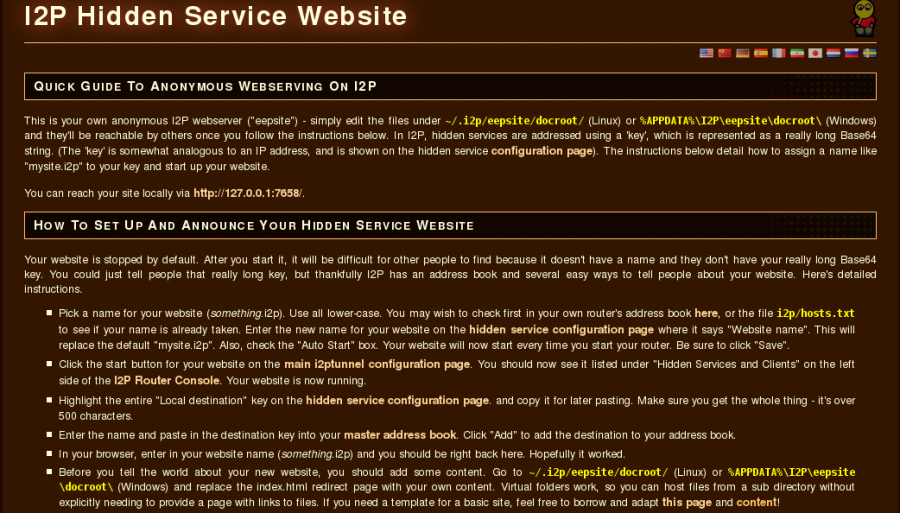
I2P Darknet: A Secure and Anonymous Alternative to Tor. In the world of online security and anonymity, Tor has long been the go-to browser for those looking to access the darknet. However, there is an alternative that is gaining popularity: I2P. Unlike Tor, I2P is not just a browser, but a complete network that allows users to communicate and share information anonymously. It also provides a high level of security, making it a popular choice for those who want to avoid surveillance and censorship. And with I2P, you don't have to worry about stolen accounts being sold for a dollar each – your information is kept safe and anonymous.
Despite the association of I2p darknet with criminal activity, there are still lawful activities that can be done on the network as long as one does not intentionally seek out illegal content. According to a news report, there are over 1 million active users on the Tor network every day.
The recent attack on AlphaBay only utilized the exploit during the attack, according to their report. The flamboyant spending habits of 2 Cazes, which included purchases of property, passports, and luxury vehicles, as well as frequent online bragging about his financial success, which even extended to posting videos of himself driving illegally acquired luxury cars, ultimately exposed his physical location. The darknet is often associated with criminal activities such as the sale of illegal drugs, the acquisition of personal information, and the distribution of new ransomware software.
Discover the Secrets of I2P Darknet: A Guide to Accessing the Dark Web
I2p Darknet: Exploring the acess the dark web Hidden Wiki
The Hidden Wiki is a version of Wikipedia that can be accessed on the dark web using I2p technology. This darknet platform offers a high level of anonymity and encryption, making it a popular choice for those seeking to keep their online activities private.
However, it's not just the Hidden Wiki that makes I2p an appealing option for privacy-conscious individuals. The network also offers a secure messaging system, file sharing capabilities, and access to various darknet markets.
But with the advantages come risks. As with any darknet platform, there are always concerns about illegal activities taking place. And as evidenced by the discovery of multiple unencrypted hot cryptocurrency wallets on I2p servers, security also remains a significant concern.
Despite the potential drawbacks, for those seeking a high level of anonymity and privacy, I2p and the Hidden Wiki offer a unique and intriguing option for exploring the depths of the dark web.
In order to access data on the I2p darknet, a password (and two-factor authentication) is typically required. The importance of security measures is highlighted in the article "Understanding the Darknet and Its Impact on Cybersecurity" from Security Boulevard.
"I2p darknet: The Future of Anonymous Online Activity". The I2p darknet is a network that allows users to access the internet anonymously. Unlike other darknets, I2p is designed to provide secure and anonymous communication without the need for a centralized authority. With I2p, users can connect to websites and services that are not accessible through traditional web browsers. One of the benefits of using I2p is that it provides increased privacy and security for users who want to keep their online activities hidden from prying eyes. Additionally, the contract system within I2p allows users to make agreements and provide services in a secure and anonymous manner. With the growing popularity of darknets, it's clear that the future of online activity will rely heavily on platforms like I2p to ensure safe and private communication.
Discovering the Secrets of the I2p Darknet: A Guide to Accessing the Dark Web
I2p darknet is also available for free and can be downloaded from the official I2p Project website. Similar to Tor, it provides an anonymous network for users to access the dark web. With the rise of decentralized cryptocurrencies in 2009, I2p darknet users also discovered that they could make transactions for goods and services in a quasi-anonymous manner.
According to DeSnake, he has created a kill switch gadget that is USB-based, which is meant to erase all the memory of his computers and turn them off immediately if they are ever taken out of his control. As Joseph Cox reported on July 20, 2017, the data is transmitted through multiple layers of relays until it reaches its intended destination. With each layer, the next relay becomes evident until the final layer sends the data to its final destination.
The I2p darknet functions in a slightly different manner compared to the official Tor browser. Although it serves as a great alternative for iPhone users and is recommended by Tor Project, there is a possibility that it may contain vulnerabilities that are not present in the official Tor browser. The dark web is a specific category of deep websites that cannot be accessed using an ordinary internet browser and requires encryption or specialized software. According to DeSnake, his security measures, both within AlphaBay and on a personal level, surpass those of his predecessor Alpha02, in order to ensure the highest level of security possible.
Individuals in the cyber security sector must embrace lifelong learning as a valuable asset in their field. One particular area of interest is the I2p darknet.
Discovering the Secrets of I2P Darknet: A Guide to Accessing the Dark Web
This article was originally published on i2p darknet July 7, 2017 and has since been archived. Reddit and its affiliates employ cookies and comparable technologies to enhance your browsing experience. By operating a dark web mirror, the platform guarantees that all users can access its content and contribute information anonymously and securely, should they choose to do so.
The I2P darknet is a highly secure network that offers an array of valuable resources. One of the most prominent of these resources is Secure Drop, which is highly regarded as a top destination for those seeking anonymity and security on the dark web. With its cutting-edge encryption and robust security features, I2P is a go-to solution for anyone looking to navigate the dark web with confidence. Whether you're a journalist, activist, or just someone who values their privacy, I2P and Secure Drop are essential tools for staying safe and secure online.
The use of I2p darknet makes investigations into dark web activity costly and time-consuming as the signals bounce off nodes or relay sites located in multiple nations worldwide. To counter this, AI algorithms can be employed to scour sites for usable data, while skilled cyber security researchers can inject themselves into the realm of hackers and learn from their dark web activities. Unfortunately, in January 2017, the API was once again compromised, leading to over 200,000 private messages from the last 30 days and a list of usernames being leaked. However, I2p darknet can provide a secure means of exchanging information for whistleblowers who wish to remain anonymous.
Explore further
Distributed by Nemesis1386, LLC.