May 04, 2023
Discover the Lucrative World of the Dark Web: The Simplest Way to Earn Money

Tracking activities on the dark web has become a crucial task for many security experts. The Network Traffic Analyzer is an effective tool that can help
trace the origin of incoming traffic and monitor where outgoing traffic is heading. Tor is a reliable web security system that ensures anonymity and privacy while browsing the web. To enhance protection against identity theft, advanced technologies are available to segment identities and enforce risk-based conditional access, allowing quick revocation of access in case of any potential threats that are detected.
Monitoring the dark web is an important task for businesses and individuals alike. With the rise of cybercrime, it's crucial to keep an eye on the activities that take place on the hidden corners of the internet. From selling stolen information to planning attacks, the dark web is a hub for criminal activity.
One way to monitor the dark web is to keep track of data leaks related to email addresses. This can provide valuable insights into potential vulnerabilities and help prevent data breaches. However, it's important to note that this service only reports on email address-related data leaks.
By staying vigilant and monitoring the dark web, individuals and businesses can better protect themselves from cyber threats and ensure the safety of their personal and sensitive information.
Can you take any productive steps to safeguard yourself from the dangers lurking in the dark web? To enhance the effectiveness of the threat intelligence system, it comprises of identified origins of phishing and impersonation assaults, that assists the security software in determining which inbound emails to deny access.
Heineken Express: A Deep Dive into the Dark Web
Monitoring the dark web is a crucial aspect of modern cybersecurity. By keeping track of illegal online activities, organizations can prevent data breaches, identity theft, and other cybercrimes. The information collected through monitoring can then be shared with other systems to gain a more comprehensive understanding of potential threats and formulate more accurate insights from the entire security stack. However, it's important to remember that all forms of communication can be used for both good and evil purposes, so it's crucial to stay vigilant and proactive in monitoring the dark web.
As per the Global Threat Report by CrowdStrike, cyber attackers are no longer relying solely on malware to steal personal information. Instead, they employ various tactics including phishing emails, which mimic legitimate email requests, to extract confidential data. It is crucial to monitor the dark web for any signs of such activities. Please note that Firefox is a trademark owned by Mozilla Foundation.
Monitoring the dark web can be an expensive endeavor, as it requires the input of both human consultants and automated scanners. The cost of such a system can be quite high due to the expertise and technology required to effectively monitor the hidden corners of the internet. However, the benefits of keeping a watchful eye on the dark web can far outweigh the cost, as it can help prevent criminal activity and protect individuals and businesses from cyber threats.
The process of monitoring the dark web is facilitated by a system which automatically collects account names and incorporates them into scans. Access to these websites is only possible through the use of a Tor browser.
CrowdStrike Security Cloud detected 62 incidents in Q4 2021 that were free of malware. The Tor network was initially developed by the US Navy to safeguard its own communication and is now utilized by various government security agencies as well as police forces globally. One such Dark Web scanner is Echosec Beacon, which assists in monitoring the hidden corners of the internet. This technology dates back to the year 2001.
Heineken Express Takes a Closer Look at the Dark Web Market
Monitoring the dark web is crucial for businesses, especially those with sensitive information. Even small businesses on tight budgets should consider investing in this category of protection. By using a monitoring tool, businesses can identify websites that mention the named person and collect information for doxing, which can lead to phishing attacks. The tool also provides customers with an account-protected dashboard that displays alerts when cyber threat intelligence related to their business is identified. Skipping this category of protection altogether is not recommended, as it can leave businesses vulnerable to potential cyber threats.
Monitoring the dark web is an essential task for organizations that want to protect their image copyright and trade secrets. By looking for usernames, passwords, and other indicators of compromise, companies can detect potential threats and take proactive measures to prevent data breaches. Moreover, using visualizations can help highlight key insights and make it easier to understand the complex web of information that exists in the dark web.
However, it is important to note that monitoring the dark web alone is not enough to ensure complete protection against cyber threats. While it can be a useful tool for detecting potential risks, it does not include threat protection software that can actively prevent attacks from occurring. It is therefore recommended that organizations implement a comprehensive security strategy that includes both dark web monitoring and threat protection software.
To address these challenges, Echosec has developed a solution that combines dark web monitoring with other security tools. By using machine learning algorithms, Echosec is able to identify potential risks and alert organizations in real-time. Additionally, Echosec's platform includes visualizations that make it easier for security teams to understand and respond to threats.
In conclusion, monitoring the dark web is an important task for organizations that want to protect their assets and prevent data breaches. While there are pros and cons to this approach, it is clear that a comprehensive security strategy that includes both dark web monitoring and threat protection software is essential for effective cyber defense.
Monitoring the dark web, also known as the Deep Web, can be just as accessible as any other website on the Clear Web. All you need is to type in the address or follow a link. However, it is important to note that you do not need to have any cybersecurity expertise to use this service, but you will need administrative skills to handle the information you receive if a threat is detected. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are all registered trademarks of NortonLifeLock Inc.
Heineken Express: Keeping a Watchful Eye on the Underbelly of the Web
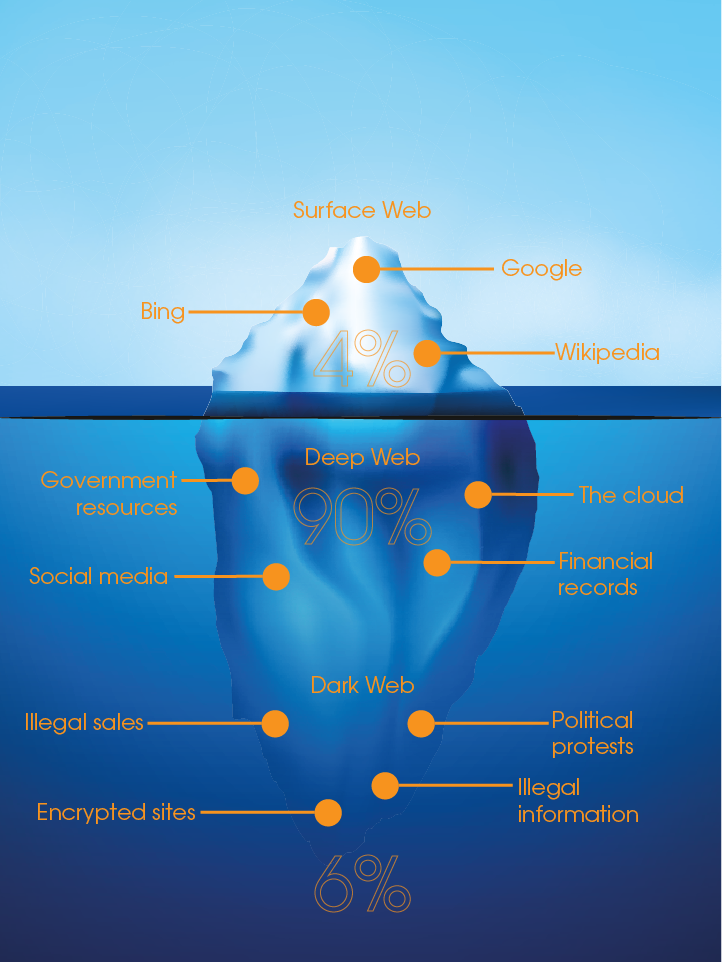
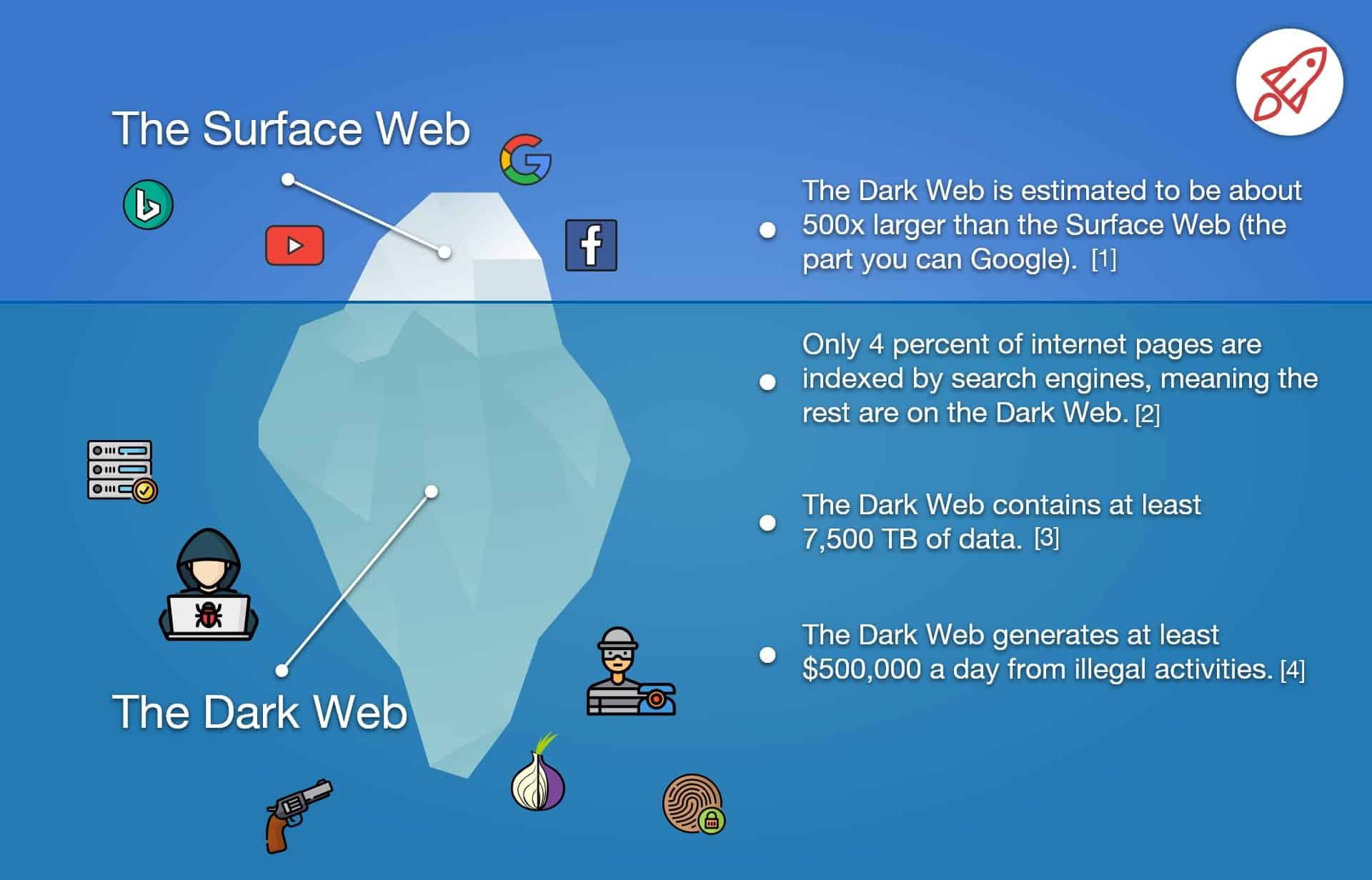
Monitoring the Dark Web is crucial in today's digital age to ensure the safety and security of individuals and organizations. With millions of websites being monitored for specific data such as corporate email addresses or general information like company name and industry, it's imperative to keep track of activities that take place in the hidden realm of the internet. The Dark Web is a secret part of the internet that requires special software to access, and it's notorious for being a hub of illegal activities such as drug trafficking, child pornography, and illegal weapon sales. By monitoring the Dark Web, organizations can take proactive measures to protect themselves from cybercriminals and stay ahead of potential threats. It's essential to have a comprehensive monitoring system that can detect and flag any illicit activities taking place, and the technology for this is constantly evolving to keep up with how to use the dark web the ever-changing landscape of the Dark Web.
If you're interested in monitoring the dark web, it's important to note that the pages on this part of the internet are not indexed by search engines and are considered part of the deep web. Unfortunately, even if you try to remove this information from other sites, it will still remain on the dark web. For those looking to protect their online privacy, using a VPN for the dark web is highly recommended.
The ATO prevention service comes equipped with a cloud-based threat intelligence database that provides clients with alerts about any compromised accounts on the dark web.
Explore further
Distributed by megbubbles88, LLC.