Apr 28, 2023
Stay Safe in the Shadows: Darknet Access and Web Monitoring Services

"Riffle: An Efficient Communication System with Strong Anonymity" (PDF). Although the darknet is teeming with fraudsters, drug dealers, smugglers, and undoubtedly terrorists as well , it is also a haven for people living in totalitarian countries and deprived of the freedom to express their opinions.
Darknet access is a highly controversial topic that has been in the news recently due to the Monachium shooting incident that occurred at the end of July 2016. Many people believe that access to the darknet is no longer supported and that it is defunct. However, there are still ways to gain access to the darknet, and it is important to be aware of the potential risks and dangers associated with using it. See also the references of Laurent Gayard's 2018 article on this topic.
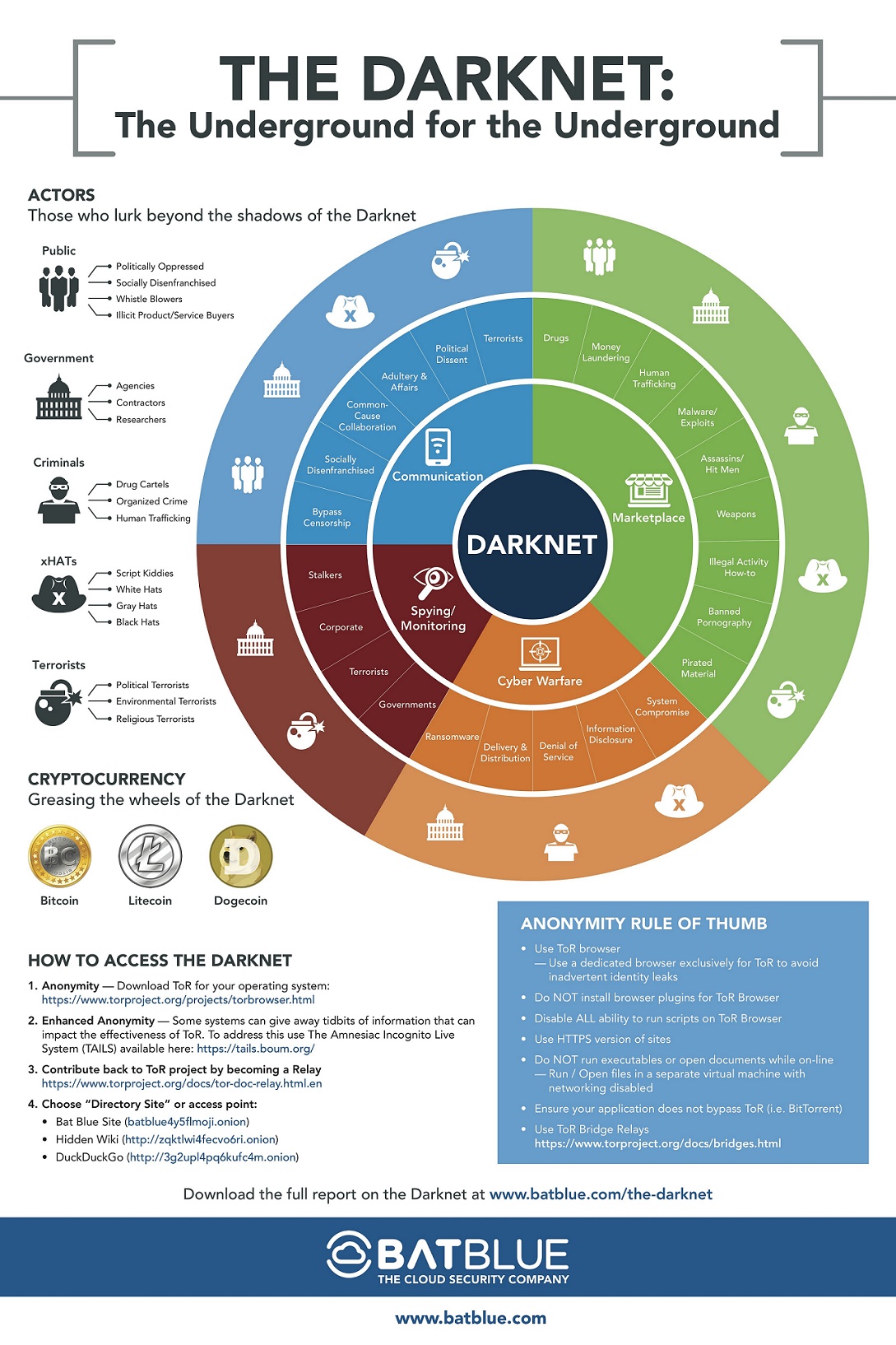
Accessing the darknet is a complex process that requires specific software and knowledge of how to use it. However, the use of the cryptocurrency Bitcoin plays an even greater role in enabling access to the darknet. Bitcoin can be used to purchase goods and services on the darknet and can also be exchanged for real currency. This allows individuals to engage in illegal activities anonymously and without fear of being traced.
Unlocking the Secrets of the Dark Web: Navigating Darknet Onion Links
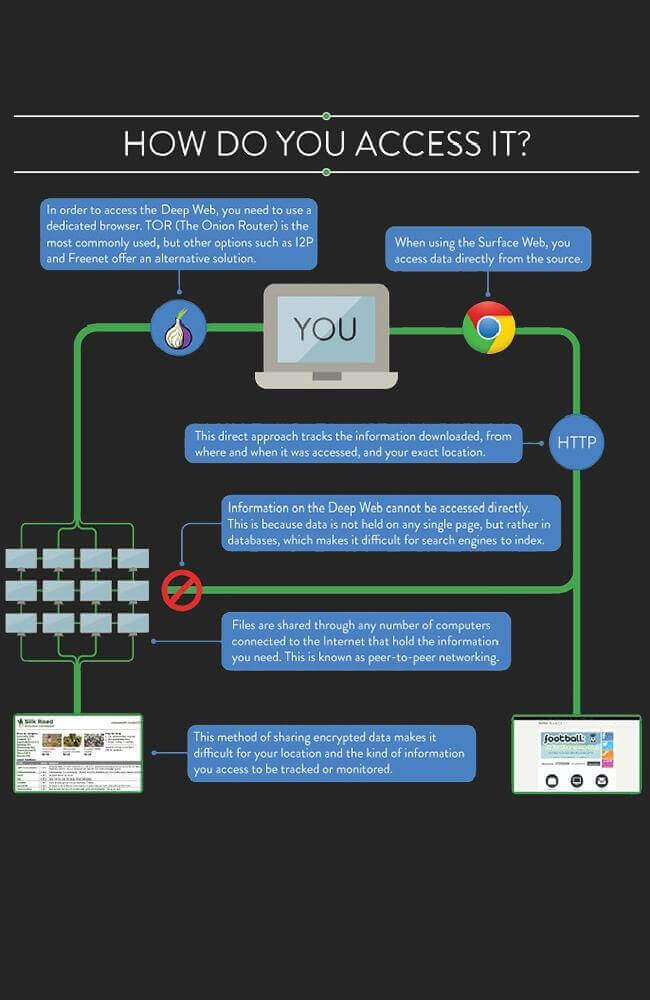
Darknet access is an intriguing topic that has caught the attention of many sub-culture enthusiasts. As a journalist, you may be wondering if you should use a VPN and Tor to access the darknet. This network is only accessible through a private network, which requires users to join by running a specific software and connecting to peers. While viewing any of its sites, anyone can join the network without any restrictions and connect with any part of it. Therefore, if you're interested in exploring this mysterious and obscure world, it's essential to take the necessary steps to protect your privacy and security.
While not essential, there are those who desire an additional layer of confidentiality when accessing the Darknet. It has been noted that combining the terms "Darknet" and "Deep Web" can be misleading, with experts suggesting that each term be used separately. A review of Jamie Bartlett's book, "The Dark Net: Inside the Digital Underworld," delves further into this topic.
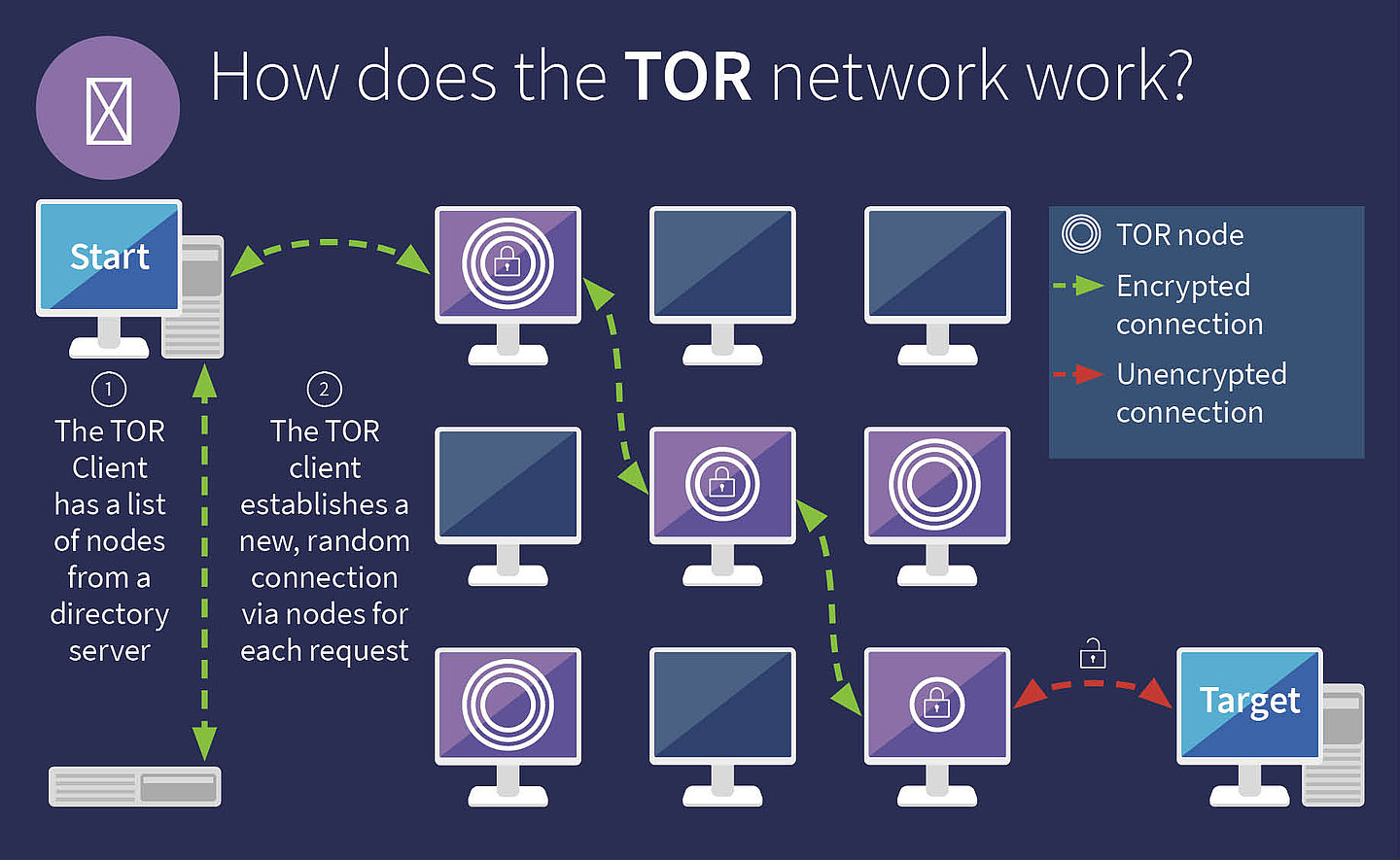
It's hard to believe what kinds of illegal goods are being traded on the darknet. The Tor browser, which is based on Firefox, will be familiar to those who have used that browser before. In addition to bouncing encrypted traffic through random nodes, the Tor browser also wipes your browsing history and deletes cookies after each session.
Discover the Secrets of Darknet Access and Onion Sites on the Dark Web
Darknet access has become a hot topic in recent years, with many people curious about how to gain access to this hidden corner of the internet. While the darknet is often associated with illegal activities, it can also be a place for people to communicate anonymously and share information without fear of censorship or surveillance.
One of the most common ways to access the darknet is through the Tor browser, which allows users to browse the internet anonymously by routing their traffic through a network of servers. However, even with Tor, it is important to exercise caution and avoid sharing personal information or engaging in illegal activities.
Other methods for accessing the darknet include using virtual private networks (VPNs) or specialized software such as Freenet or I2P. These tools can provide additional layers of security and anonymity, but again, it is important to use them responsibly and avoid engaging in illegal activities.
Overall, while the darknet can be a fascinating and useful tool for those seeking anonymity and privacy online, it is also important to remember the potential risks and dangers involved. By using caution and common sense, it is possible to explore the darknet safely and responsibly.
To delve deeper into the subject of encryption technology and the various hidden internet applications, I suggest perusing the articles by Steve Mansfield-Devine (1 December 2009). The name "darknet" was coined due to the multiple layers one must peel away to uncover the true identities of its users. The moniker "dark web" is often used interchangeably with "darknet" on account of the numerous concealed services within Tor's darknet.
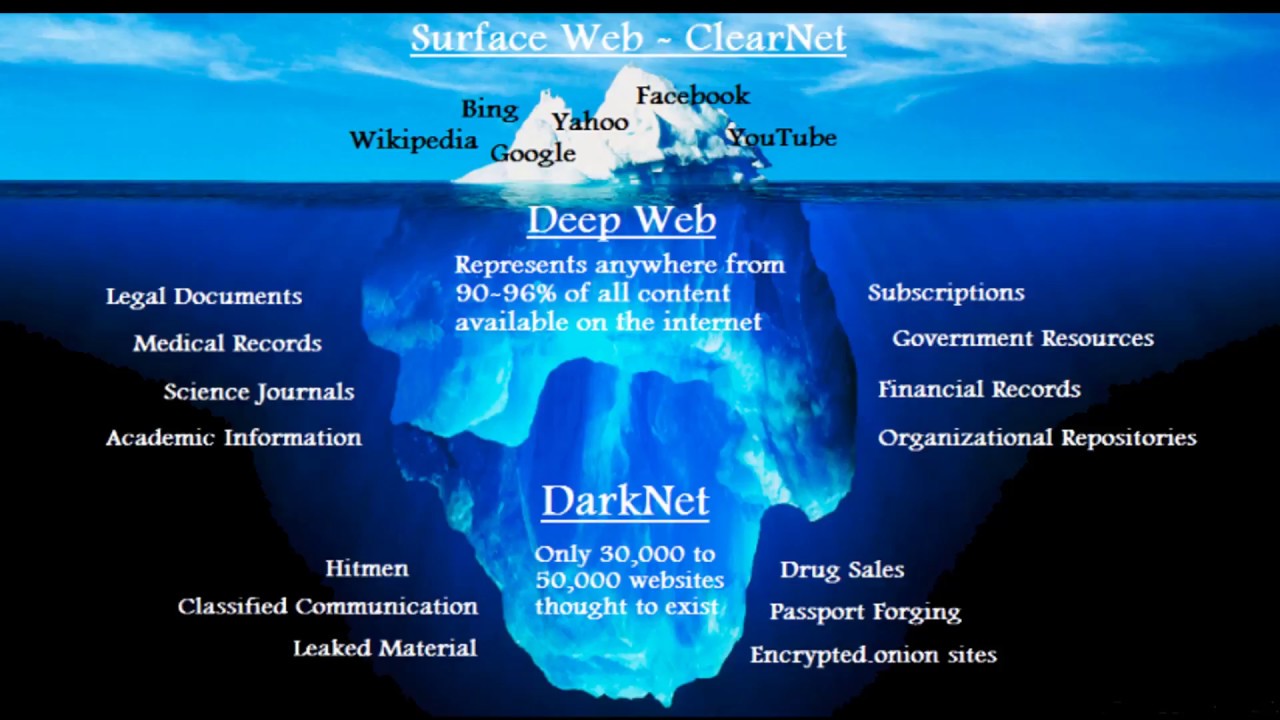
For those seeking entry into the notorious dark markets, it's advisable to begin by exploring the deep web. As previously mentioned, the deep web is not a singular entity, but rather a category of various locations that share one common feature - they are concealed from the view of search engines and average internet users.
Accessing the darknet provides scammers with an easier life than in the regular internet. If someone purchases a weapon on the darknet and does not receive the product, they are unlikely to report it to the police. DeepDotWeb occasionally covers this topic. Doi:.1016/S1361-3723(09)70150-2.
Darknet access can be achieved through either the friend-to-friend or opennet modes.
Unlocking the Secrets of the Dark Web
Darknet access refers to the ability to enter an overlay network within the Internet that can only be accessed with specific software, configurations, or authorization. This network often utilizes a unique communication protocol that is customized for security purposes. One example of such software is "SecureDrop".
Maybe you are concerned about your online privacy and security and are intrigued by the concept of an internet space where users are not constantly tracked, monitored, and analyzed by manipulative marketers, government spies, and malicious hackers. By exercising caution and using a combination of the Tor browser and common sense in selecting which sites to access on the dark web, it is possible to use it safely. The dark web is known to host pirated copies of films and TV shows, pornography, illegal licenses for software, counterfeit luxury watches, stolen credit card information, PayPal or Netflix accounts, and identity documents.
Explore further
Distributed by GPexa, LLC.