Apr 29, 2023
Discover the Secrets of the Darknet Tor: Unveiling the Black Market

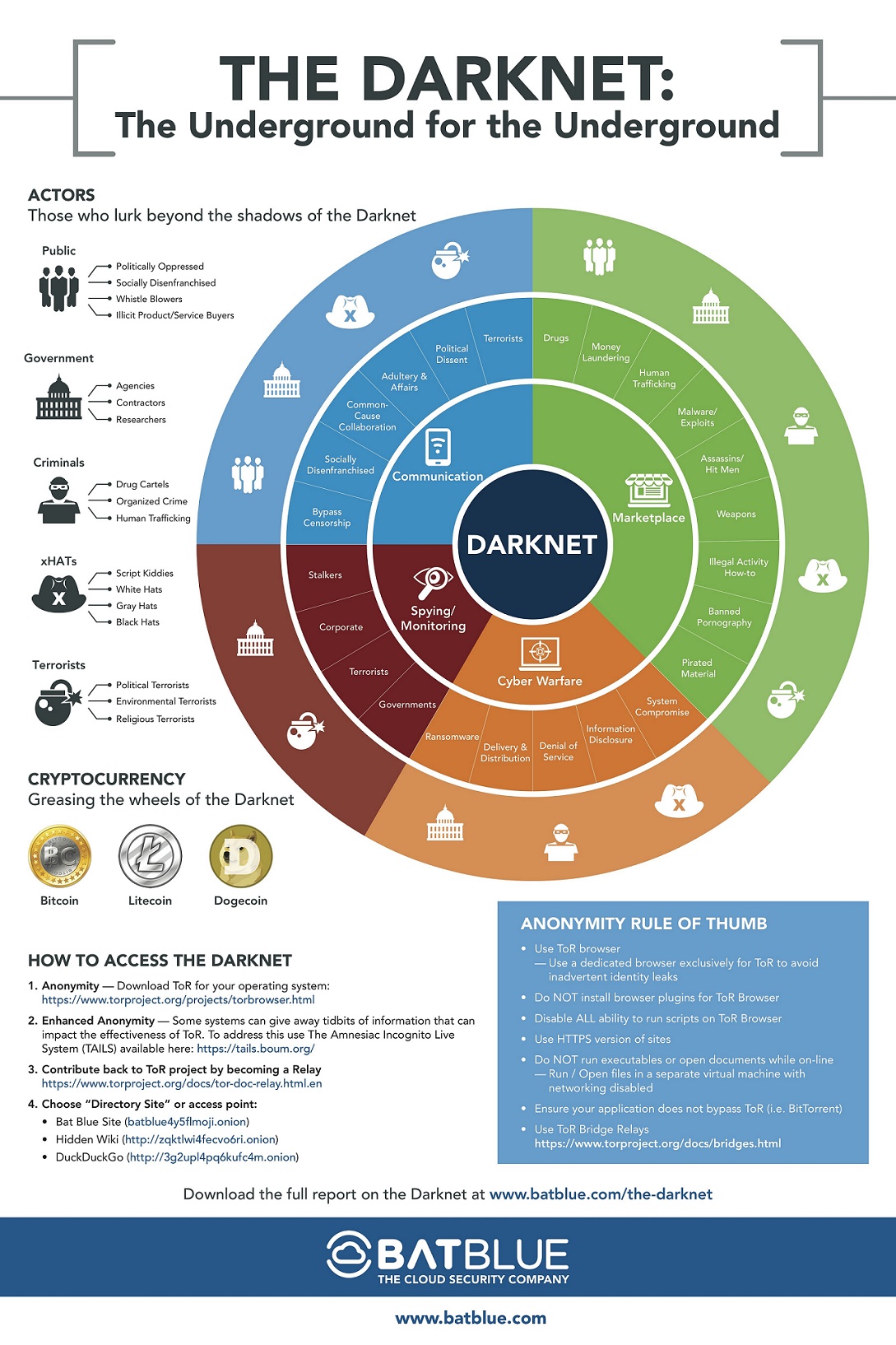
Darknet is a network that operates on the Tor network, which is a free and open-source software that allows anonymous communication. The Darknet is a section of the internet that is not indexed by search engines, and can only be accessed through specific software or configurations. It is known for being a haven for illegal activities such as drug dealing, weapons trading, and human trafficking. The Tor network operates by using encryption and multiple layers of routing to ensure that users remain anonymous and their activities cannot be traced back to them. While the Darknet can be a dangerous place, it is also used by journalists, activists, and whistleblowers who need to communicate safely and anonymously. Overall, the Darknet remains a mysterious and controversial corner of the internet that continues to fascinate and intrigue people around the world.
The term "Darknet tor" is often associated with illegal activities and criminal groups. The dark web is infamous for its involvement in various illicit activities. However, there are also legitimate uses for accessing the dark web, such as whistleblowing and anonymous browsing. Some news organizations even monitor these sites for breaking news. iOS users can access the dark web using OnionBrowser to protect their anonymity while browsing.
Get a Glimpse of the Dark Side with Tor Browser for Dark Web
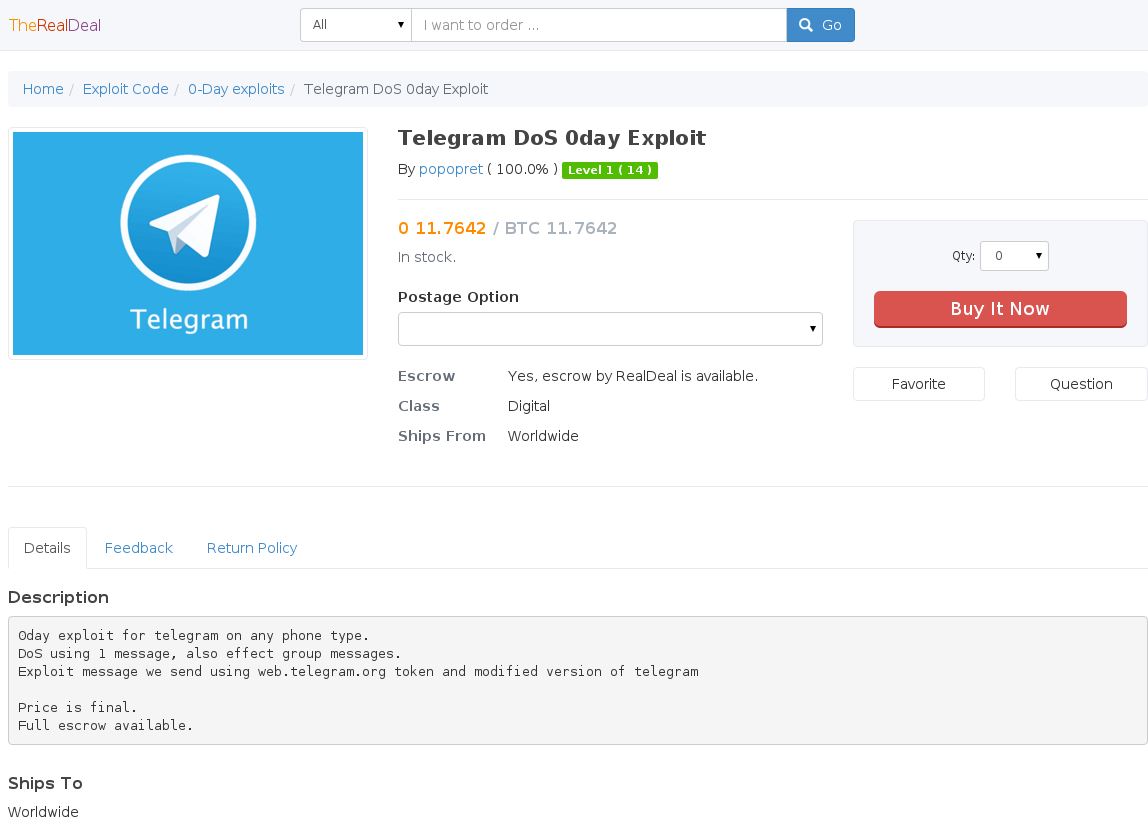
Darknet tor is a platform that provides access to a variety of illegal and unethical activities. It offers services like DDoS attacks and botnets access, which can be used for malicious purposes. Additionally, it provides access to remote access Trojans (RATs), keyloggers, and exploits that can be used for espionage and other nefarious activities. However, despite the lousy performance, unpredictable availability, and occasional shock factor of the dark web, it is still worth a visit for those who can tolerate it. There are also practical benefits for some organizations who may find value in these services.
Understanding the Working of Darknet Tor
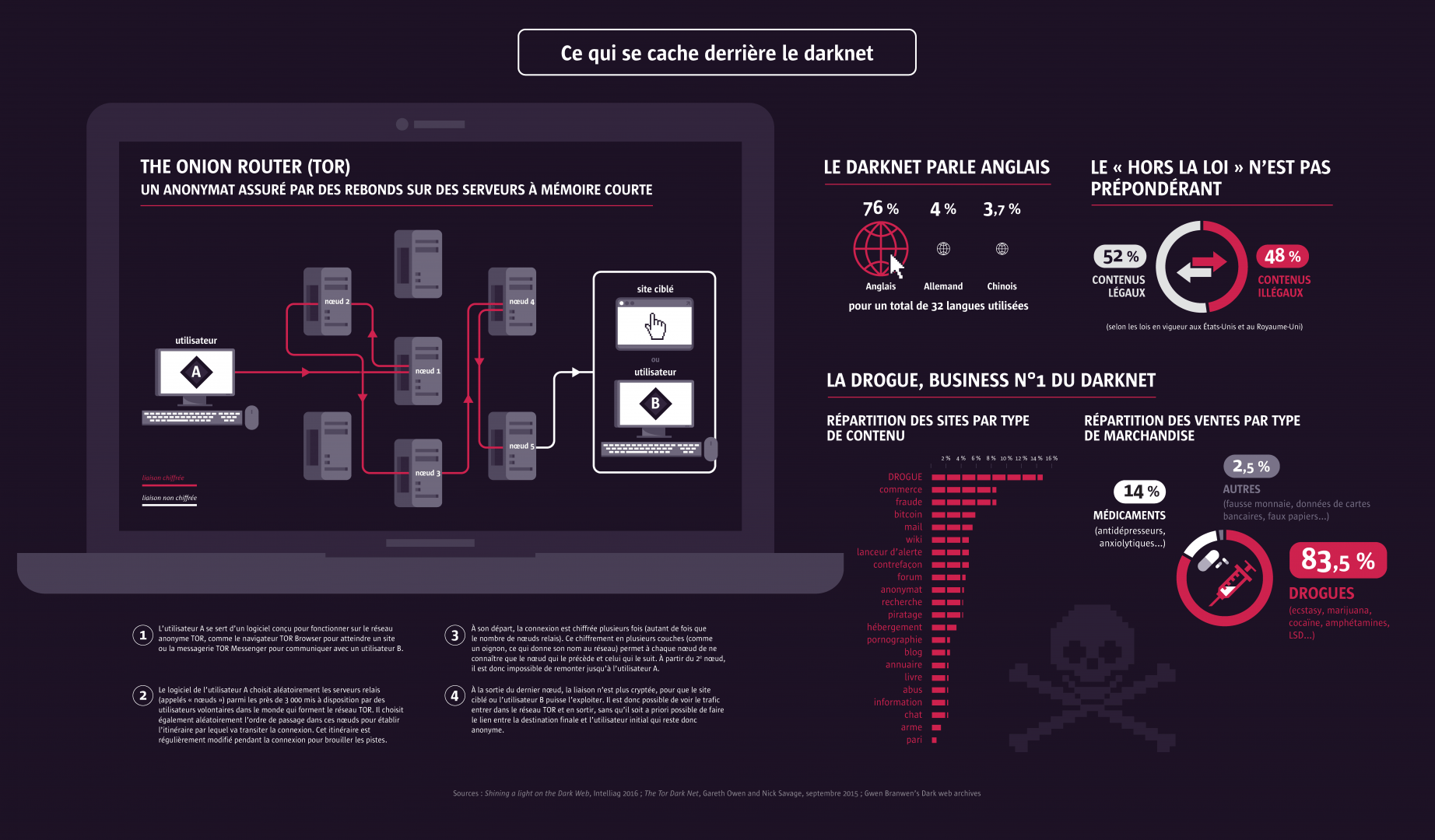
The Tor network is an advanced system that routes TCP traffic of all types, with a specific focus on web browsing optimization. By using Tor, users can access the Darknet, a hidden network of websites that cannot be accessed through traditional search engines. Tor works by encrypting user data and bouncing it around a network of servers, making it almost impossible for anyone to track the user's online activities. Tor offers anonymity, security, and privacy to users, making it a popular tool for those who want to keep their online activities hidden from prying eyes.
The dark web or darknet is a place where many tools can be utilized to monitor and scan for personal information. In addition, there are tools available to respond to any potential attacks. Our mission is to promote human rights and safeguard online privacy through the use of free software and open networks. Nowadays, the dark web has become a popular tourist destination.
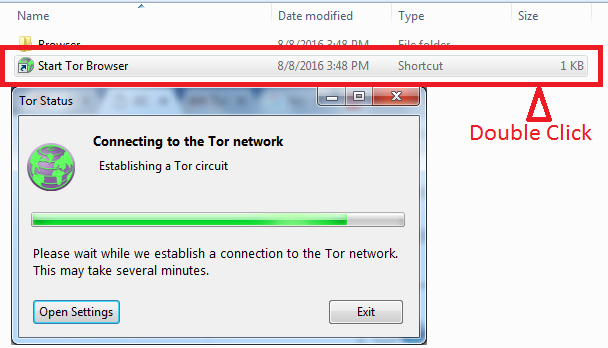
If you find that a website you usually access through Tor suddenly displays a 404 error, it is possible that the service is intentionally blocking Tor traffic without any valid reason. This can have severe consequences for businesses, as it may lead to disruptions in their operations due to DDoS attacks or other types of malware. To avoid such situations, it is essential to know how to use the Tor Browser properly.
Discover the Secrets of Darknet Tor - Diving into the Depths of the Dark Web
The Darknet tor provides a veil of secrecy for criminals to carry out their malicious activities. However, this privacy should not be exclusive to lawbreakers. We must take action to level the playing field and ensure that privacy is a fundamental right for all. For instance, I utilize the Darknet tor to stay informed about potential threats and monitor ongoing events, as it allows me to maintain situational awareness.
When it comes to accessing the Darknet, the most common way to do so is through Tor (The Onion Router). This network is a collection of servers that allow users to browse the internet anonymously. Unlike the clear web, which can be accessed through standard web browsers, the Darknet can only be accessed through specialized software. While the Darknet is often associated with illegal activities like drug sales and cybercrime, it can also be used for legitimate purposes such as secure communication and anonymous whistleblowing.
Darknet Tor is a platform where certain groups create and distribute advanced malware, often in conjunction with existing tools, via third-party partners. However, it is important to note that Tor does not solely enable criminal activity.
The topic of Darknet Tor has been a subject of interest for many individuals lately. It is a network that provides anonymity to its users by allowing them to access the internet through a series of encrypted layers. There are various support services available on the Darknet Tor, including tutorials, credentials, phishing, refunds, customer data, operational data, financial data, intellectual property/trade secrets, and other emerging threats. The report on Darknet Tor also outlined three risk variables for each category, which could result in devaluing the enterprise, such as undermining brand trust.
For most people who are reading this article, it is important to note that using Tor Browser is completely legal. However, it is important to remember that nearly all dark web commerce sites conduct transactions in Bitcoin or its variants. This does not necessarily mean that it is safe to do business on the Darknet Tor.
As individuals who are willing to break laws, they already have access to numerous alternatives that offer greater privacy than what Tor can offer.
The Darknet tor has its origins dating back to the late 13th century, coinciding with the founding of the city. Recently, in the summer of 2017, a group of cyber law enforcement officers from three different nations managed to successfully close down AlphaBay, the largest source of illegal goods on the dark web, causing a ripple effect throughout the network. Due to constant DDoS attacks, websites on the Darknet tor are constantly changing their addresses, making for a highly dynamic environment.
The Darknet tor is a thriving and profitable business model.
The Shadowy World of Tor: Where to Score Your Drugs
Tor is a platform created to safeguard the privacy and security of law-abiding individuals. The deep web is a part of Tor that remains hidden from search engines. Interestingly, the district of 7 faced damage from German Luftwaffe bombings during the Invasion of Poland in 1939.
Explore the Darknet with Tor Browser, which allows you to bypass restrictions imposed by your home network. Despite the availability of search engines like Grams, the search results can be repetitive and irrelevant to your query. The Dark Web Price Index 2021 by Privacy Affair reveals the latest prices of various data and services traded on the dark web. For instance, a cloned credit card with PIN can cost you anywhere from 25 to 35 credits.
According to estimates, the deep web encompasses between 96 and 99 percent of the entire internet. One of the most well-known components of the deep web is the darknet, which can only be accessed through specialized software like Tor. The darknet is notorious for being a hub of illegal activity, including the sale of drugs, weapons, and stolen data. However, it is also used by activists, journalists, and whistleblowers who need to communicate and share information anonymously. While the darknet may have a negative reputation, it is important to remember that it also serves a valuable purpose in protecting privacy and enabling free speech.
The structure was dark web sex embellished with attic spaces and four towers on each side. The darknet has search engines of its own, though even the most advanced ones struggle to keep up with the ever-changing terrain. Cybercriminals use various methods to defraud businesses, ranging from stealing intellectual property to engaging in espionage that hampers a company's competitiveness or results in direct financial damage.
Despite its intimidating moniker, not all of the dark web is utilized for unlawful activities. One example of this is the Tor network, which is a decentralized system that allows users to browse the internet anonymously. While some people do use Tor to access illegal services and content, many others use it for legitimate purposes such as protecting their privacy and freedom of speech. In fact, Tor has been used by journalists, activists, and whistleblowers to anonymously communicate and share information with the public. However, it's important to note that using Tor does not guarantee complete anonymity and there are still risks involved. As with any technology, it can be used for both good and bad purposes and it's up to the individual to use it responsibly.
Explore further
Distributed by schellsob, LLC.